Forensics in Linux. Dumping Memory, Disks, and Network Connections to Find Further Evidence
The first task in digital forensics is collecting information, specifically, obtaining images of hard drives and RAM, and, if that can help, dumping network connections. In this article, we'll see what you need to do to get all this on a Linux machine, and learn some other useful skills along the way.
This is a new part of the forensic cycle for beginners, in which we talk about what digital forensics is, analyze the most popular analysis tools, study several cases on Android devices, and investigate the theft of funds from the RBS system on a Windows 10 laptop
. cycle:
First of all, I recommend installing the Auditd utility on live systems - it can be used to get detailed information about system changes in audit mode.
First of all, we will be interested in such events as:
Some features of forensics in Linux
In the last article, which was devoted to the case of embezzlement of funds in RBS on Windows 10, we used, if possible, programs with a graphical interface as a toolkit. If you do not take proprietary solutions, such as, for example, EnCase Forensic or Belkasoft Evidence Center , then on Linux, most working utilities run in command line mode.
Using test commands saves a lot of time on software manipulation, but, on the other hand, it can be too complicated for beginners. However, beginners usually do not do forensics!
In addition to individual utilities, there are entire distributions designed for digital forensics. First of all , these are DEFT , CAINE , Sumuri PALADIN , Helix , and, of course, the well-known Kali Linux . A complete overview of distributions and toolkits for forensics can be found in the article “ Toolkit for forensics. We choose a distribution kit and a set of software for forensic analysis .
From the literature on forensics in Linux, I would first of all recommend almost the only full-fledged book about this. It was written by Philip Polstra and is called Linux Forensics Paperback . Secondly, the UNIX and Linux Forensic Analysis DVD Toolkit by Chris Pogue and others. And thirdly, Digital Forensics with Kali Linux .
General verification checklist
To search and collect forensic evidence, we will first create images (dumps) of the following objects of our systems:
Since the hardware on which the entire farm runs is located in a reliable data center, the search for artifacts related to the network file system (NFS) , locally mounted devices and USB-connected devices is immediately swept aside.
Always think carefully about what kind of action and for what purpose you are doing. Incorrect use of the programs given in the text of the article can lead to loss of information (artifacts) or distortion of the data obtained (forensic evidence). Neither the author nor the editors are responsible for any damage caused by misuse of the material in this article.
We remove the HDD image
It is quite possible to remove a sector-by-sector copy of the hard disk without resorting to additional utilities. We will use the old and tested native tool dd . It allows you to create exact bitwise copies - both of entire disks, and of individual partitions, and even just files.
Removing disk images and working with them using regular system tools can lead to unintentional recording, which is impossible in serious forensics. Read the details in the article "Toolkit for Forensics" (section "How not to inherit the pathfinder"). Use the commands below only if you think it's appropriate for you.
But first, we will ask the system for a complete list of partitions using the fdisk command :
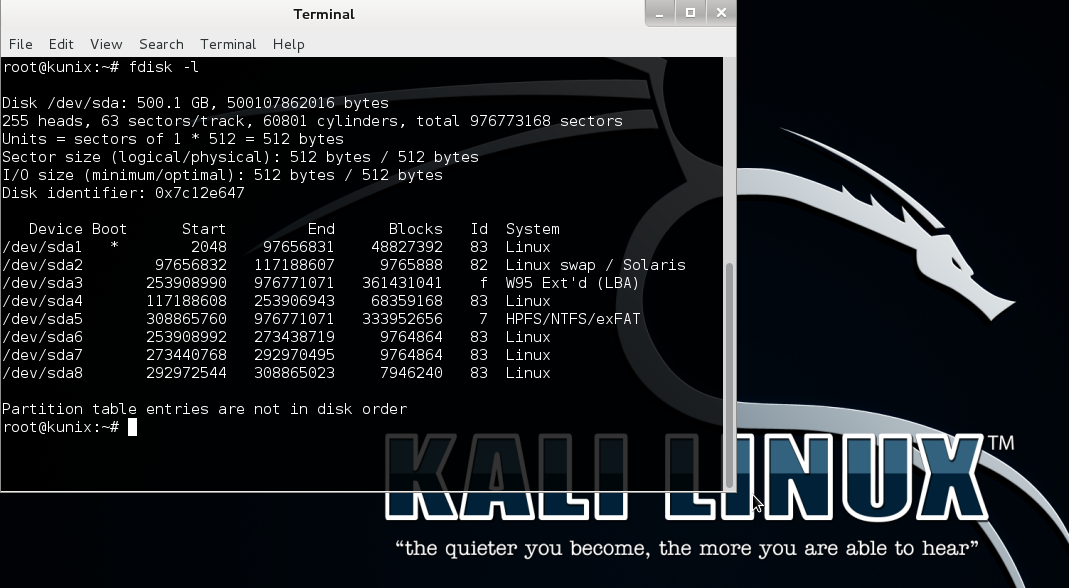
Listing Filesystems
The basic syntax for dd is:
The first task in digital forensics is collecting information, specifically, obtaining images of hard drives and RAM, and, if that can help, dumping network connections. In this article, we'll see what you need to do to get all this on a Linux machine, and learn some other useful skills along the way.
This is a new part of the forensic cycle for beginners, in which we talk about what digital forensics is, analyze the most popular analysis tools, study several cases on Android devices, and investigate the theft of funds from the RBS system on a Windows 10 laptop
. cycle:
- "Theory, books, courses, useful materials"
- “We find data sources, search and analyze artifacts”
- Android under the hood. How cases of hacking mobile devices are revealed»
- “The Mystery of the Treasury Notebook. Use Forensics to Solve a Heist"
First of all, I recommend installing the Auditd utility on live systems - it can be used to get detailed information about system changes in audit mode.
First of all, we will be interested in such events as:
- system startup and shutdown (reboot, shutdown);
- reading / writing system files and changing access rights to them;
- initiating a network connection and changing network settings;
- change information about a user or group;
- changing the date and time;
- installing, removing, starting and stopping programs and daemons;
- making system calls.
Some features of forensics in Linux
In the last article, which was devoted to the case of embezzlement of funds in RBS on Windows 10, we used, if possible, programs with a graphical interface as a toolkit. If you do not take proprietary solutions, such as, for example, EnCase Forensic or Belkasoft Evidence Center , then on Linux, most working utilities run in command line mode.
Using test commands saves a lot of time on software manipulation, but, on the other hand, it can be too complicated for beginners. However, beginners usually do not do forensics!
In addition to individual utilities, there are entire distributions designed for digital forensics. First of all , these are DEFT , CAINE , Sumuri PALADIN , Helix , and, of course, the well-known Kali Linux . A complete overview of distributions and toolkits for forensics can be found in the article “ Toolkit for forensics. We choose a distribution kit and a set of software for forensic analysis .
From the literature on forensics in Linux, I would first of all recommend almost the only full-fledged book about this. It was written by Philip Polstra and is called Linux Forensics Paperback . Secondly, the UNIX and Linux Forensic Analysis DVD Toolkit by Chris Pogue and others. And thirdly, Digital Forensics with Kali Linux .
General verification checklist
To search and collect forensic evidence, we will first create images (dumps) of the following objects of our systems:
- RAM (system and user processes, daemons, possibly running malicious code, and so on);
- hard disk (sector-by-sector copy of the HDD, including deleted partitions, unallocated disk areas, worn files, hidden files and directories, etc.);
- network stack (raised connections, open ports, "unknown" services on ports, spurious traffic).
- on the list of users, groups, privileges;
- processes running as root;
- scheduled tasks (cron jobs);
- files with SUID and SGID bits set ;
- the composition of the file /etc/sudoers ;
- hidden files and directories;
- files opened for reading in the system;
- network interfaces, connections, ports, routing table;
- логи iptables, fail2ban (Reports, Alarms, Alerts);
- configuration /etc/ssh/sshd_config;
- Syslog daemon logs (check for typical alerts );
- SELinux state;
- list of loaded kernel modules.
Since the hardware on which the entire farm runs is located in a reliable data center, the search for artifacts related to the network file system (NFS) , locally mounted devices and USB-connected devices is immediately swept aside.
Always think carefully about what kind of action and for what purpose you are doing. Incorrect use of the programs given in the text of the article can lead to loss of information (artifacts) or distortion of the data obtained (forensic evidence). Neither the author nor the editors are responsible for any damage caused by misuse of the material in this article.
We remove the HDD image
It is quite possible to remove a sector-by-sector copy of the hard disk without resorting to additional utilities. We will use the old and tested native tool dd . It allows you to create exact bitwise copies - both of entire disks, and of individual partitions, and even just files.
Removing disk images and working with them using regular system tools can lead to unintentional recording, which is impossible in serious forensics. Read the details in the article "Toolkit for Forensics" (section "How not to inherit the pathfinder"). Use the commands below only if you think it's appropriate for you.
But first, we will ask the system for a complete list of partitions using the fdisk command :
QUOTE:
$ fdisk -l

Listing Filesystems
The basic syntax for dd is:
You must reply before you can see the hidden data contained here.

