Hello Friends!! Today we are going to take another CTF challenge named “Born2Root: 2”.
It is available on the Vulnhub website. Although there is no description provided at the current time on the Vulnhub website, we assume that we will have to gain the root access and find a flag.
Security Level: Intermediate
Step 01-: scanning the network to find our target {NETWORK SCANNING}
command/tool -: netdiscover
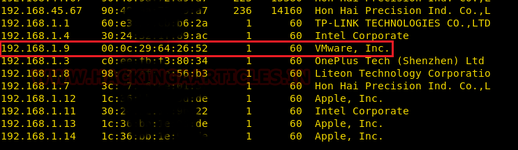

We found out target: 192.168.1.9
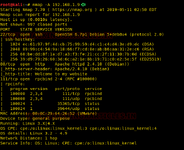
Time to scan the Target’s IP with nmap. Nmap scan result shows 3 major ports open, 22(SSH), 88(HTTP) and 111(RPC).
Command -: nmap -A 192.168.1.9
Since port 80 is running HTTP, so we considered opening the Target IP Address on the Browser. This gives us an attractive looking webpage although after spending a considerable amount of time. We found that this is nothing but a distraction. We couldn’t find anything of importance on the website.
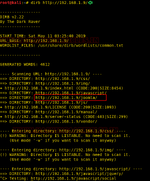
So now we moved on to try the Directory Bruteforcing to get any hints. The drib scan gives us the Joomla directory. This is a major breakthrough. Now it’s time to exploit machine through Joomla.
command-: dirb http://192.168.1.9/
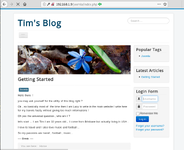
Now that we have found the joomla directory, we will browse the joomla directory on our browser. Here we have the blog made by the author. This is titled Tim’s Blog. This could be a hint for a username. Let’s keep that in mind. Now as we can see that we have a Login Form in the bottom right. Now we will have to guess the user credentials.
Now, it is by convention to try the default credentials first. A quick search, informs us that the default username for Joomla is ‘admin’. Now for the password, we will have to perform a dictionary attack. For that, we will create a dictionary from the words present on the webpage using ‘cewl’.
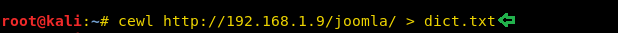
command-: cewl http://192.168.1.9/joomla/ > dict.txt
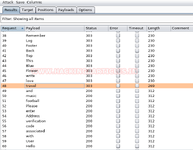
Now that we have the dictionary named dict.txt. Its time to perform the bruteforce. We will use the BurpSuite to perform the bruteforce. To learn more about this, refer to this article. This bruteforce force gives us “travel” as the password.
Now we will use these credentials to login in Joomla:
Username: admin
Password: travel
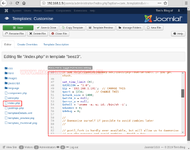
Now that we have logged in on the Joomla as the SuperUser. To exploit the Joomla server, we will use the php reverse shell. They can be found in Kali Linux. We will move on to the Template Section. To do so, we will first click on the Extensions Option on the Menu. Then, traverse in the beez3 template and choose Customise. This is open an edit section as shown in the image. Now, select the index.php and replace the text inside the index.php with our reverse shell. Remember to change the IP Address and/or change the port.
After editing the index.php, save the file by clicking on the Save Button. Now we have successfully replaced the index.php with our reverse shell script. Now, all that’s left to do is run the index.php. Now to get a session, we need a listener, where we will get our reverse shell. We will use netcat for creating a listener as shown in the image given below.
After we got the shell, now it was time to enumerate the machine in order to exploit further. It took us a couple of hours of hard work around the machine. We ran a bunch of scripts and much else. At last, our search at the ended when we stumbled upon the opt directory. Inside this directory, we found the scripts directory and that "contained the fileshare.py". Upon close inspection of the fileshare.py file, we got the login credentials as shown in the given image.
commands-:
nc -lvp 1234
python -c 'import pty;pty.spawn("/bin/bash")'
cd /opt
ls
cd scripts
ls
cat fileshare.py
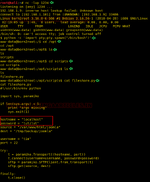
After finding the credentials all that was left was to login as Tim. For that we used the su command and gave the following credentials:
Username: tim
Password: lulzlol
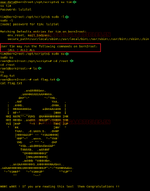
After logging in as Tim, we ran the sudo with -l parameter to give us the user rights of the user tim. As we can see in the given image, tim has all the permissions. After this, we traversed inside the root directory using the cd command. Here we found the final flag.
Commands-:
su tim
sudo -l
sudo su
cd /root
ls
cat flag.txt
Finally Voila !!! You completed it!!. ~ Team HOH {Hellofhackers}
@CyberGod @CyberDemon
It is available on the Vulnhub website. Although there is no description provided at the current time on the Vulnhub website, we assume that we will have to gain the root access and find a flag.
Security Level: Intermediate
Penetrating Methodology
- Scanning
- Enumeration
- Exploitation
- Privilege Escalation
- Capture the Flag
Walkthrough-:
Step 01-: scanning the network to find our target {NETWORK SCANNING}
command/tool -: netdiscover


We found out target: 192.168.1.9
Time to scan the Target’s IP with nmap. Nmap scan result shows 3 major ports open, 22(SSH), 88(HTTP) and 111(RPC).
Command -: nmap -A 192.168.1.9

Since port 80 is running HTTP, so we considered opening the Target IP Address on the Browser. This gives us an attractive looking webpage although after spending a considerable amount of time. We found that this is nothing but a distraction. We couldn’t find anything of importance on the website.

So now we moved on to try the Directory Bruteforcing to get any hints. The drib scan gives us the Joomla directory. This is a major breakthrough. Now it’s time to exploit machine through Joomla.
command-: dirb http://192.168.1.9/

Now that we have found the joomla directory, we will browse the joomla directory on our browser. Here we have the blog made by the author. This is titled Tim’s Blog. This could be a hint for a username. Let’s keep that in mind. Now as we can see that we have a Login Form in the bottom right. Now we will have to guess the user credentials.

Now, it is by convention to try the default credentials first. A quick search, informs us that the default username for Joomla is ‘admin’. Now for the password, we will have to perform a dictionary attack. For that, we will create a dictionary from the words present on the webpage using ‘cewl’.
command-: cewl http://192.168.1.9/joomla/ > dict.txt
Now that we have the dictionary named dict.txt. Its time to perform the bruteforce. We will use the BurpSuite to perform the bruteforce. To learn more about this, refer to this article. This bruteforce force gives us “travel” as the password.

Now we will use these credentials to login in Joomla:
Username: admin
Password: travel
Now that we have logged in on the Joomla as the SuperUser. To exploit the Joomla server, we will use the php reverse shell. They can be found in Kali Linux. We will move on to the Template Section. To do so, we will first click on the Extensions Option on the Menu. Then, traverse in the beez3 template and choose Customise. This is open an edit section as shown in the image. Now, select the index.php and replace the text inside the index.php with our reverse shell. Remember to change the IP Address and/or change the port.

After editing the index.php, save the file by clicking on the Save Button. Now we have successfully replaced the index.php with our reverse shell script. Now, all that’s left to do is run the index.php. Now to get a session, we need a listener, where we will get our reverse shell. We will use netcat for creating a listener as shown in the image given below.
After we got the shell, now it was time to enumerate the machine in order to exploit further. It took us a couple of hours of hard work around the machine. We ran a bunch of scripts and much else. At last, our search at the ended when we stumbled upon the opt directory. Inside this directory, we found the scripts directory and that "contained the fileshare.py". Upon close inspection of the fileshare.py file, we got the login credentials as shown in the given image.
commands-:
nc -lvp 1234
python -c 'import pty;pty.spawn("/bin/bash")'
cd /opt
ls
cd scripts
ls
cat fileshare.py

After finding the credentials all that was left was to login as Tim. For that we used the su command and gave the following credentials:
Username: tim
Password: lulzlol
After logging in as Tim, we ran the sudo with -l parameter to give us the user rights of the user tim. As we can see in the given image, tim has all the permissions. After this, we traversed inside the root directory using the cd command. Here we found the final flag.
Commands-:
su tim
sudo -l
sudo su
cd /root
ls
cat flag.txt

Finally Voila !!! You completed it!!. ~ Team HOH {Hellofhackers}
@CyberGod @CyberDemon

