HashTag.py is a Python script written to parse and identify the password hash type used.
HashTag supports the identification of over 250 hash types along with matching them to over 110 hashcat modes (use the command line switch -hc to output the hashcat modes). It is also able to identify a single hash, parse a single file and identify the hashes within it, or traverse a root directory and all subdirectories for potential hash files and identify any hashes found.
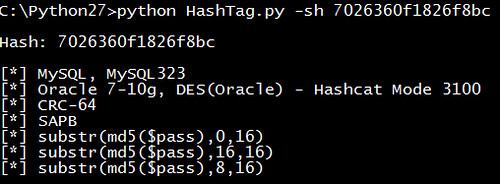
One of the biggest aspects of this tool is the identification of password hashes. The main attributes used to distinguish between hash types are character set (hexadecimal, alphanumeric, etc.), hash length, hash format (e.g. 32 character hash followed by a colon and a salt), and any specific substrings (e.g. ‘$1$’). A lot of password hash strings can’t be identified as one specific hash type based on these attributes. For example, MD5 and NTLM hashes are both 32 character hexadecimal strings. In these cases the author made an exhaustive list of possible types and has the tool output reflect that.
It has three main arguments:
You can download HashTag here:
HashTag supports the identification of over 250 hash types along with matching them to over 110 hashcat modes (use the command line switch -hc to output the hashcat modes). It is also able to identify a single hash, parse a single file and identify the hashes within it, or traverse a root directory and all subdirectories for potential hash files and identify any hashes found.
One of the biggest aspects of this tool is the identification of password hashes. The main attributes used to distinguish between hash types are character set (hexadecimal, alphanumeric, etc.), hash length, hash format (e.g. 32 character hash followed by a colon and a salt), and any specific substrings (e.g. ‘$1$’). A lot of password hash strings can’t be identified as one specific hash type based on these attributes. For example, MD5 and NTLM hashes are both 32 character hexadecimal strings. In these cases the author made an exhaustive list of possible types and has the tool output reflect that.

It has three main arguments:
- Identifying a single hash type (-sh)
- Parsing and identifying multiple hashes from a file (-f)
- Traversing subdirectories to locate files which contain hashes and parse/identify them (-d)
| 1 | HashTag.py {-sh hash |-f file |-d directory} [-o output_filename] [-hc] [-n] |
You can download HashTag here:
You must reply before you can see the hidden data contained here.

